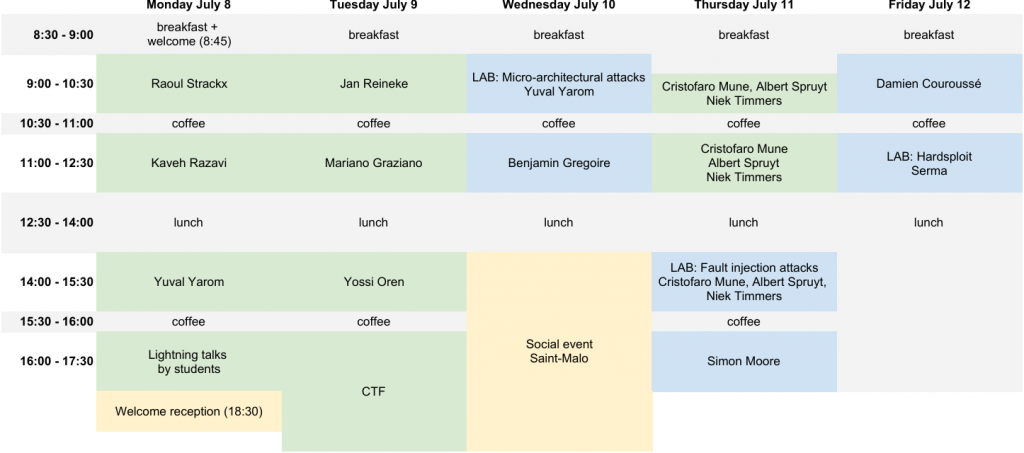
The summer school will start on Monday, July 8 in the morning, and finish on Friday, July 12 after lunch.
The program comprises:
- Lectures and labs by our speakers.
- Lightning talks of 5 to 10 minutes by students who registered.
- Social events: a welcome cocktail at Rennes city hall on Monday, July 8, and an afternoon of activities in Saint-Malo followed by a gala dinner on Wednesday, July 10.
Green sessions (lectures and CTF) will take place at Inria.
Blue sessions (lectures and labs) will take place at CentraleSupélec.
Yellow sessions will take place outside.
CTF: Capture All The SILM{flags}
Capture All The SILM{flags}, or CATS, is a CTF event taking place Tuesday afternoon, which welcomes participants of all levels, the only requirements being an interest in cybersecurity and wanting to have fun! What is a CTF, you say? It is a Capture the Flag competition, where you get to solve challenges, and earn flags (and points)! If you haven’t participated in one before, this is the perfect chance to do so. The challenges will be from a wide range of categories, such as cryptography, web security, reverse engineering, and pwn, and we know everyone will find something interesting to solve. Keep an eye on your inboxes for some pre-CTF information and teasers!
More information on the CTF page.
Monday, July 8
Morning — 8:45-12:30, Inria
| 8:15-8:45 | Breakfast |
| 8:45-9:00 | Welcome |
| 9:00-10:30 | Raoul Strackx, KU Leuven (Belgium) [slides] [video] Title: Page table based side-channel attacks against Intel SGX: Attacks and Defenses Abstract: Intel SGX is a recent Intel technology first shipped with its Skylake processors in 2015. It’s design goal is to provide strong isolation properties of code and data in so called ‘enclaves’ and this even against kernel or hypervisor layer attackers. It does so by ensuring that enclaves can only be accessed through specific entry points they expose. All other access attempts are prevented by hardware. Intel SGX enclaves live in the address space of the process that created them. This implies that enclaves still need to use the (untrusted) page tables, but any translation is verified by SGX hardware. Access restrictions at the page-table level (e.g., non-present pages) are still enforced. This opens up interesting side-channel attacks: An attacker may mark an enclave page as not-present. She then executes the enclave. If she receives a page fault, she has learned that that page contained code or data that was required during the execution of the enclave, and vice versa. This simple attack can be extended to extract very sensitive data from enclaves. While simple in concept, this side-channel attack has proven to be very challenging to mitigate. No silver-bullet solution has been found. |
| 10:30-11:00 | Coffee break |
| 11:00-12:30 | Kaveh Razavi, Vrije Universiteit Amsterdam (Netherlands) [slides] [video] Title: Reverse Engineering Hardware for Fun and Profit Abstract: Recent years have shown that the basic principles on which we rely on for building secure computing systems do not always hold. Memory is plagued with disturbance errors and processors leak sensitive information across security boundaries. At the core of these discoveries you can often find gruesome and heroic reverse engineering efforts. In this talk, I will discuss some examples where we have used a variety of r verse engineering techniques from timing, to cold boot and fault attacks to gain the knowledge that is necessary for building sophisticated microarchitectural and rowhammer attacks. |
Lunch — 12:30-14:00, Inria
Afternoon — 14:00-17:30, Inria
| 14:00-15:30 | Yuval Yarom, University of Adelaide and Data61 (Australia) [slides] [video] Title: An Introduction to Microarchitectural Attacks Abstract: To achieve the performance requirements of modern age computation, the microarchitectural design of processors deviates from the intuitive model programmers use. Multiple techniques for exploiting the discrepancy between the two models to leak information between programs have been developed in recent years. This talk discusses the basic mechanisms that enable these attacks and presents a few examples of attacks. |
| 15:30-16:00 | Coffee break |
| 16:00-17:30 | Lightning talks by participants
|
Social event — 18:30-19:30, City center
| 18:30-19:30 | Welcome reception at Rennes City Hall We will go by bus as a group to the city center. Bus tickets will be provided. |
Tuesday, July 9
Morning — 9:00-12:30, Inria
| 8:30-9:00 | Breakfast |
| 9:00-10:30 | Jan Reineke, Saarland University (Germany) [slides] [video] Title: SPECTECTOR: Principled Detection of Speculative Information Flows Abstract: Since the advent of Spectre, a number of countermeasures have been proposed and deployed. Rigorously reasoning about their effectiveness, however, requires a well-defined notion of security against speculative execution attacks, which has been missing until now. We present a novel, principled approach for reasoning about software defenses against Spectre-style attacks. Our approach builds on speculative non-interference, the first semantic notion of security against speculative execution attacks. We develop SPECTECTOR, an algorithm based on symbolic execution to automatically prove speculative non-interference, or to detect violations. |
| 10:30-11:00 | Coffee break |
| 11:00-12:30 | Mariano Graziano, Cisco Talos (Italy) [slides] [video] Title: Research and automation in a modern security company Abstract: Over the years, the number of unique samples collected per day by security companies increased exponentially. In this presentation we will see how security researchers can cope with this overwhelming number of malware samples. We will show from where all these samples are collected and how they can be effectively processed by state-of-the-art techniques. Moreover, we will discuss how other executable file formats such as ELF are gaining popularity and how we as a community need new tools to analyze and dissect these new and challenging threats. Finally, we will show how automation is a key point for a security company for either large-scale and manual analyses. |
Lunch — 12:30-14:00, Inria
Afternoon — 14:00-16:00, Inria
| 14:00-15:30 | Yossi Oren, Ben-Gurion University (Israel) [slides] [video] Title: Side-Channel Attacks on Human Secrets Abstract: Side-channel analysis techniques have been traditionally applied toward the recovery of computer-related secrets such as cryptographic keys. Humans, however, also share secrets of their own with their computers – for example, their browsing habits, their political or religious beliefs, or sensitive information about their health. This secret information is increasingly vulnerable to emerging low-cost side-channel attacks that are highly scalable, employing malicious peripheral devices or turning components of a system against itself. There are countermeasures which can be applied to protect systems from the theft of human secrets via side channel attacks. These countermeasures, however, have different designs, and exact different costs, than those designed to protect against the theft of cryptographic secrets. |
| 15:30-16:00 | Coffee break |
Social event: CTF — 16:00-20:30, Inria
| 16:00-20:30 | CATS CTF Beginners and CTF experts all welcome to our CTF. There will even be pizza! |
Wednesday, July 10
Morning — 9:00-12:30, CentraleSupélec
| 8:30-9:00 | Breakfast |
| 9:00-10:30 | Yuval Yarom, University of Adelaide and Data61 (Australia) LAB: Mastik: a Toolkit for Microarchitectural Attacks Abstract: While the mechanisms underlying microarchitectural attacks are understood, implementing the attacks is challenging due to the need to bridge between the clean theory presented in research publications and the realities of the undocumented processor behaviour these rely upon. Mastik, a toolkit for microarchitectural side channel attacks, aims to bridge this gap. It aims to provide a set of primitives that implement known attack techniques, to allow researchers to experiment with the attacks and with defences. In this lab we will experiment with Mastik and gain practical experience with microarchitectural attacks. |
| 10:30-11:00 | Coffee break |
| 11:00-12:30 | Benjamin Grégoire, Inria (France) [video] Title: Formal Verification of Masked Implementation Abstract: Masking is a popular countermeasure to protect implementations against differential power analysis. The security guarantees of software and also hardware masking can advantageously be captured through formal models. The existence of such models has been instrumental to the emergence of fully automated methods for analyzing masked implementations. The tutorial will present an overview of MaskVerif, a tool to check security of maked implementations. We will start with a brief introduction on differential power analysis and masking and quickly get to a survey of existing models for evaluating the security of masked software and hardware implementations. It will include the threshold probing model, and its variants to support transitions and glitches, the noisy leakage model, and the bounded moment model. We shall then give a unified framework that captures all these settings. We will then give an overview of the different techniques used by MaskVerif for proving security of concrete implementations in these models. The second part of the lecture will discuss the problem of secure composition. It has been shown that popular security notions used in the context of masking do not compose if used without care. However, recent work provides solutions to this problem. We will describe available methods for achieving secure composition. |
Lunch — 12:30-13:30, CentraleSupélec
Social event — 13:30-23:30, Excursion to Saint-Malo
| 13:30-23:30 | Excursion to Saint-Malo Activities according to your registration: catamaran, guided tour, free time. The excursion will be followed by a dinner. |
Thursday, July 11
Morning — 9:30-12:30, Inria
| 9:00-9:30 | Breakfast |
| 9:30-10:45 | Cristofaro Mune, Pulse Security (Malta), Albert Spruyt, Independent (Netherlands), Niek Timmers, Independant (Netherlands) [slides Session #1] [slides Session #2] [video] Title: PEW PEW PEW: A Primer On Fault Injection Abstract: – Session #1: In this session we will introduce the concept of fault injection to the students. We will explain what fault injection is, its terminology and what effect it may have on a chip’s behavior. This session will form the foundation to put the remaining sessions into context. – Session #2: In this session we will describe what type of attacks can be performed once an attacker is able to inject a glitch. We will explain one attack during boot (e.g. bypassing secure boot) and one attack during runtime (e.g. escalating privileges in Linux). |
| 10:45-11:15 | Coffee break |
| 11:15-12:30 | Cristofaro Mune, Pulse Security (Malta), Albert Spruyt, Independent (Netherlands), Niek Timmers, Independant (Netherlands) [slides Session #3] [slides Session #4] [video] Title: PEW PEW PEW: A Primer On Fault Injection (continued) Abstract: – Session #3: In this session we will explain what fault models are and why it is important to formalize the effect of fault injection. This session will form the foundation for the next session where we explain how fault models can be used to attack and defend devices. – Session #4: In this session we will explain how fault injection fault models can be used for offensive and defensive purposes. The students will learn that formalizing the effect of a glitch on a chip is fundamental to develop both innovative attacks and defenses. This session will provide the foundation for the workshop where the students will be triggered to attack and defend a secure boot implementation. This lecture will provide your with sufficient background to partake in the afternoon workshop. Requirements: None |
Lunch — 12:30-14:00, Inria
Afternoon — 14:00-17:30, CentraleSupélec
| 14:00-15:30 | Cristofaro Mune, Pulse Security (Malta), Albert Spruyt, Independent (Netherlands), Niek Timmers, Independant (Netherlands) Title: Attacking an Hardening Secure Boot LAB: In our fault injection workshop, you will be triggered to partake in discussing how fault injection can be used to bypass secure boot as implemented by ARM Trusted Firmware (https://www.trustedfirmware.org/about/). Next to this offensive focus, we will trigger you into discussing what can be done to harden this secure boot implementation against fault injection attacks. We plan to provide you an emulated version of the secure boot implementation we use throughout the workshop. This allows you to continue after the workshop has finished in order to put your hypothetical attacks and defenses in practice. Requirements: – PC computer with at least 40 GB free space – VMware Player 10 or higher – Our VM (should be shared before the workshop) |
| 15:30-16:00 | Coffee break |
| 16:00-17:30 | Simon Moore, University of Cambridge (UK) [slides CHERI] [slides Thunderclap] [video] Title: Winning the war in memory using CHERI capabilities Abstract: Many recent wide-spread security incidents (WannaCry, Heartbleed, CloudBleed, StackClash) have been due to memory safety bugs. To mitigate these vulnerabilities, we propose to use capabilities: software managed but hardware enforced tokens of authority used to access memory. We demonstrate that capabilities can be used for memory safety, preventing the root cause of many attacks. Extensions to capabilities provide very efficient fine grained compartmentalisation, allowing the principle of least privilege to be expressed, thereby mitigating many known and unknown attacks. The full stack solution has been completed, including the processor, compiler, linker, operating system and evaluation of a large corpus of applications. |
Friday, July 12
Morning — 9:00-12:30, CentraleSupélec
| 8:30-9:00 | Breakfast |
| 9:00-10:30 | Damien Couroussé, CEA LIST (France) [slides] [video] Title: Side-Channel Attacks and Software Countermeasures Abstract: Side-Channel Attacks and Fault Injection Attacks are the two sides of the same threat, here the attacker exploits a physical access to the target device. Those attacks are very powerful because they break the standard assumptions about the security of cryptographic primitives: by exploiting the (very) partial knowlegde of the implementation of a secured component, it is possible to ‘break’ the security of this component. In the world of physical attacks, the security assumptions provided by traditional cryptanalysis need to be reconsidered. E.g. the stream cipher AES, otherwise considered secure, needs to be protected against such attacks. In this tutorial, we will introduce the working principle of side-channel attacks, and discuss in-depth side-channel attacks based on power and electromagnetic observations. We will show how it is possible to recover a secret cipher key using Correlation Power Analysis. We will then introduce the principles of the main countermeasures against side-channel attacks; we will observe their impact on the effectiveness of side-channel attacks, and their limits. Finally, we will discuss about existing solutions to secure software implementations against side-channel attacks. |
| 10:30-11:00 | Coffee break |
| 11:00-13:00 | Mazlum Duman, SERMA Safety Security (France) Title: Hacking embedded systems & IoT training LAB: This training aims to understand the security weaknesses of embedded systems, master attack techniques used by hackers and ways to limit their impacts. Learn to secure embedded systems from the design phase and understand vulnerabilities necessary for risk mitigation. |
Lunch — 13:00-14:00, CentraleSupélec